RSA有毒
- Jarvis OJ Medium RSA
- Jarvis OJ hard RSA
- Jarvis OJ very hard RSA
- Jarvis OJ Extremely hard RSA
- God Like RSA
Jarvis OJ Medium RSA
首先用如下命令得到n的值
1 | openssl rsa -noout -text -inform PEM -in pubkey.pem -pubin |
n的值如下
1 | 0x00c2636ae5c3d8e43ffb97ab09028f1aac6c0bf6cd3d70ebca281bffe97fbe30dd |
做素数分解得到p和q,编写如下代码得到flag,注意解密得到的16进制是基数位,所以从第二位开始以ascii码输出
1 | import binascii |
flag如下
1 | PCTF{256b_i5_m3dium} |
Jarvis OJ hard RSA
拿到这个题目发现和上一题非常相似,连n都是一样,但是这里的e = 2。一开始还是想像上一题一样的解法,然而,它果然不会让人这么轻易拿到flag。隐隐约约记得老师上课的时候讲过模n二次根的算法,一翻发现了Rabin公钥密码,是这个没跑了。然后我们用二次符号判断enc(mod p)和enc(mod q)是否是p或q的平方剩余。
1 | root@localhost:~/Temp# python |
经过上述判断,我们就可以用存在二次根的数x1和x2求解二次根,最后用中国剩余定理得到明文
1 | import gmpy2 |
得到flag为
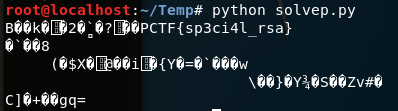
Jarvis OJ very hard RSA
通过加密代码可知,这两个加密文件共用了模数,自然想到模数攻击,其原理如下
$$
c_1 = m^{e_1} \mod n
$$
$$
c_2 = m^{e_2}\mod n
$$
$$
若e_1和e_2互素,有re_1+se_2 = 1,则可以根据
$$
$$
(c_1)^r*(c2)^s = m^{re_1+se_2} = m \mod n
$$
所以编写solve.py如下
1 | import binascii |
得到flag如下
1 | PCTF{M4st3r_oF_Number_Th3ory} |